Building Modern Applications with Security Embedded - DevSecOps > Vulnerable Container Application > Configuring Security Policy
Configuring Security Policy
Protect your application with Application Security
1. Open the Trend Micro Cloud One console and log in.

2. Select the Application Security tile.
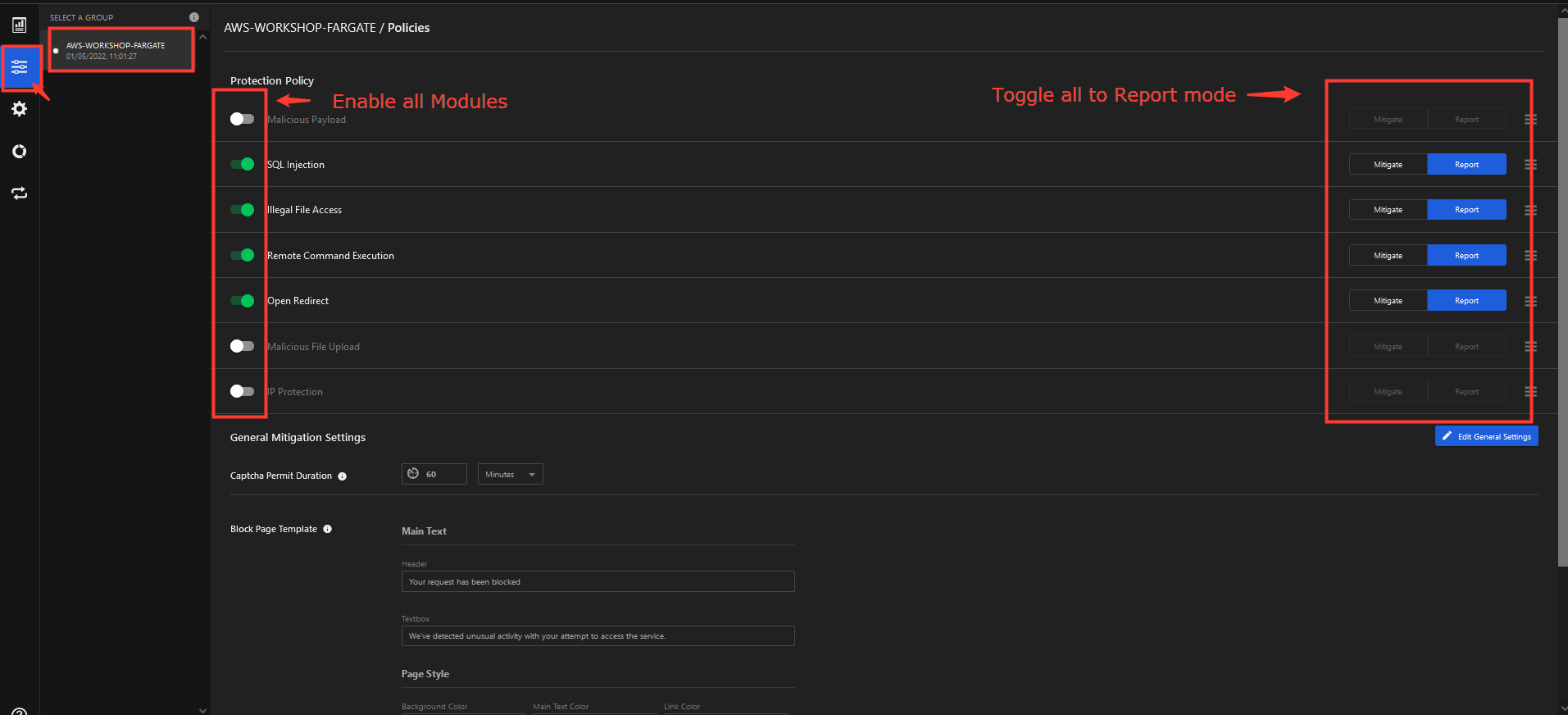
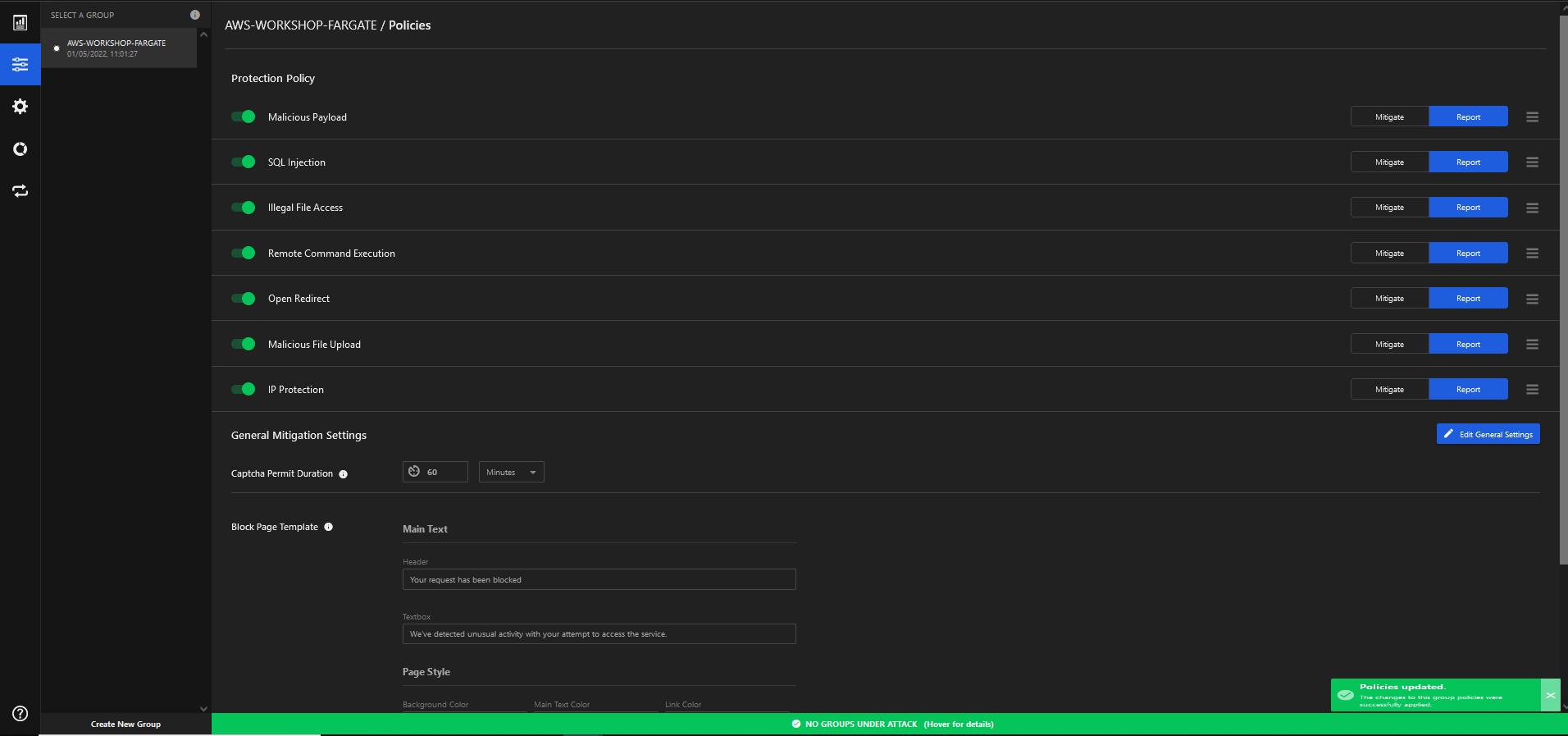
3. Select the AWS-WORKSHOP-FARGATE security group created previously and edit the policy.
- Ensure all modules are ENABLED
- Ensure all modules are in REPORT mode.
- Save
4. Open your AWS management console and log in.
- Navigate to Amazon ECS
- Select our created Cluster
- Select Tasks Tab
- Select your Task ID to obtain the Public IP address
- Using our Jump-Box RDP session, in a FireFox browser paste the IP address and port:
your.ip.address:8000
5. Create a fake user and log in with the user created
Example:
- Username:
aws-workshop - Password:
L3tsL3arn
Now let’s start the attacks tests 💻 🚀