Vulnerable Lambda
How Application Security embedded agent can protect Lambda
To understand how it works better, let’s start by deploying the serverless app on your AWS environment ☁️
1. Open and log into the Trend Micro Cloud One console.
Open the Trend Micro Cloud One console and select the Application Security tile.

2. Create a new security group
- Click Create New Group
- Group Name: AWS-WORKSHOP-LAMBDA
- Create Group

NOTE: After creating the group you will be given credentials needed for the Application Security agent.

3. Launch the CloudFormation template provided for the Lambda application that will be deployed.
The Application Security agent has been automatically added in the CloudFormation template. The steps used to deploy the agent will be covered later in the workshop.
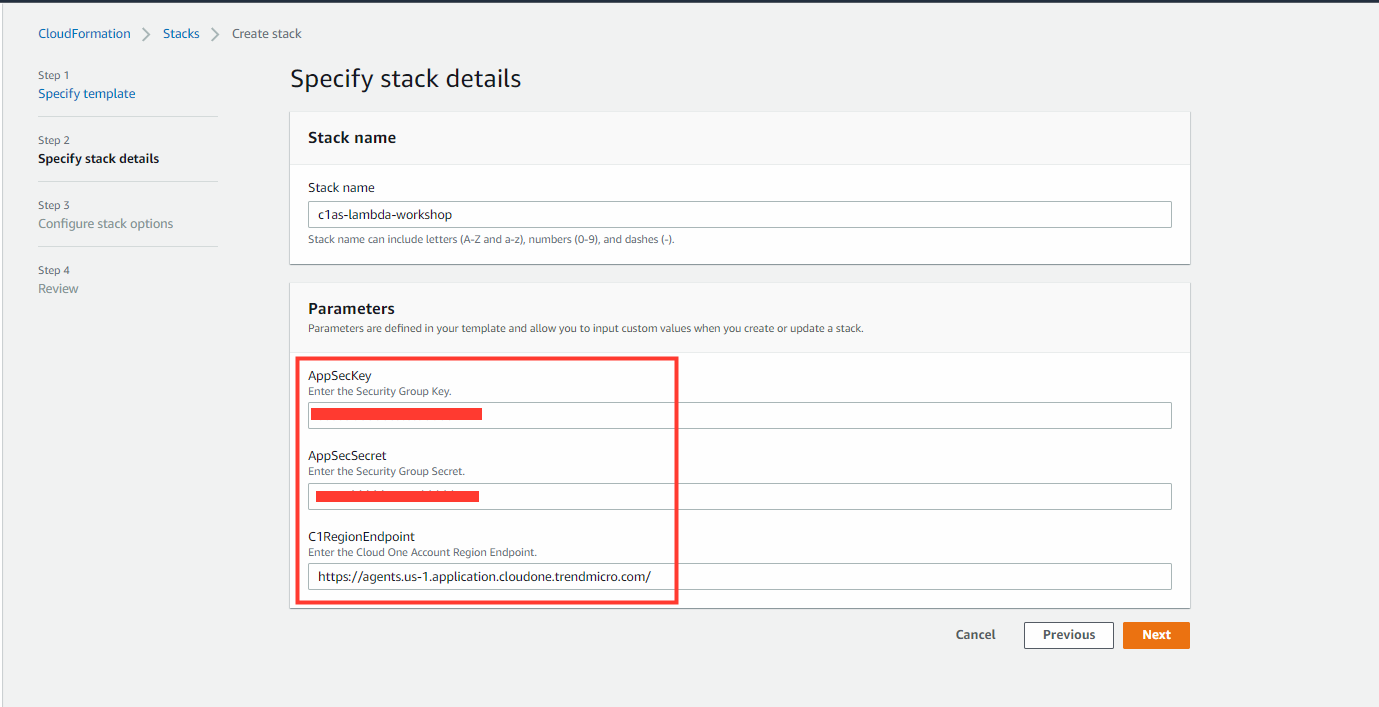
4. Provide both the Trend Micro Cloud One region endpoint and security group secret and key.
- Stack Name:
c1as-lambda-workshop - C1RegionEndpoint:
https://agents.us-1.application.cloudone.trendmicro.com/ - Security Group Key
In Trend Micro Cloud One Console - Security Group Secret
In Trend Micro Cloud One Console
⚠️ In our use case we are using Region US-1(US) on Trend Micro Cloud One. If you will be using a different region, please change the URL to your proper region based on the Trend Micro Cloud One documentation
5. When the stack finishes, under the OutPuts tab, obtain the website URL created.
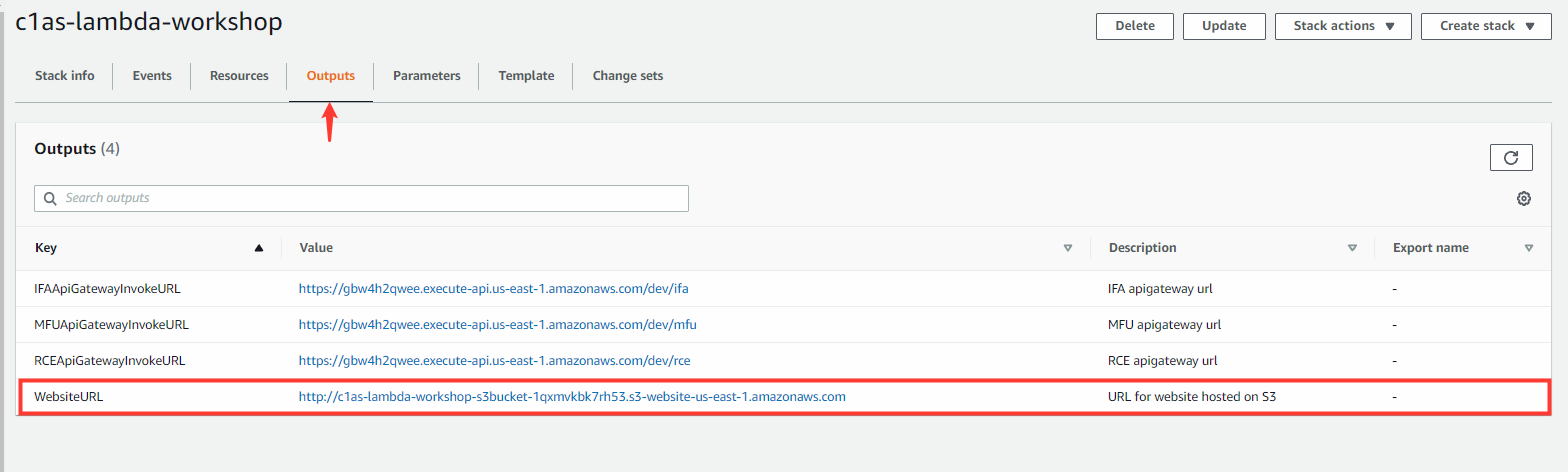
6. In the Jump-Box open FireFox, and navigate to the website URL provided to ensure app is functioning.

You have successfully deployed the vulnerable serverless application on Lambda. This web app serves as learning tool and alerts you that the app is not secure, as opposed to real-world applications, which are not as illuminating.
Application Security provides runtime protection for serverless functions from within by providing a security layer that can be configured to protect the Lambda function. As a result, both the function code and the third-party packages leveraged by the function code are automatically protected.
Lambda provides two ways to package and deploy the serverless functions:
- Functions packaged as archive
- Functions packaged as container images
📌 For more information on Container Images to protect Lambda click here
When Lambda functions are packaged as an archive, the runtime protection can be enabled by configuring the Lambda function to include the Application Security layer for Lambda, which contains the security algorithms that are protecting the functions.
How is the agent integrated with Lambda?
Adding protection to your Lambda function is simple and only requires adding the Application Security layer and adding the required configuration for the handler and the security layer (without any change to the function source code). The installation and configuration are dependent on the function programming language and on the version of Amazon Linux.
Configuring the protection layer in Lambda.
- Select our previously deployed stack
- Select Resources tab
- Search and select the function: IfaLambdaFunction
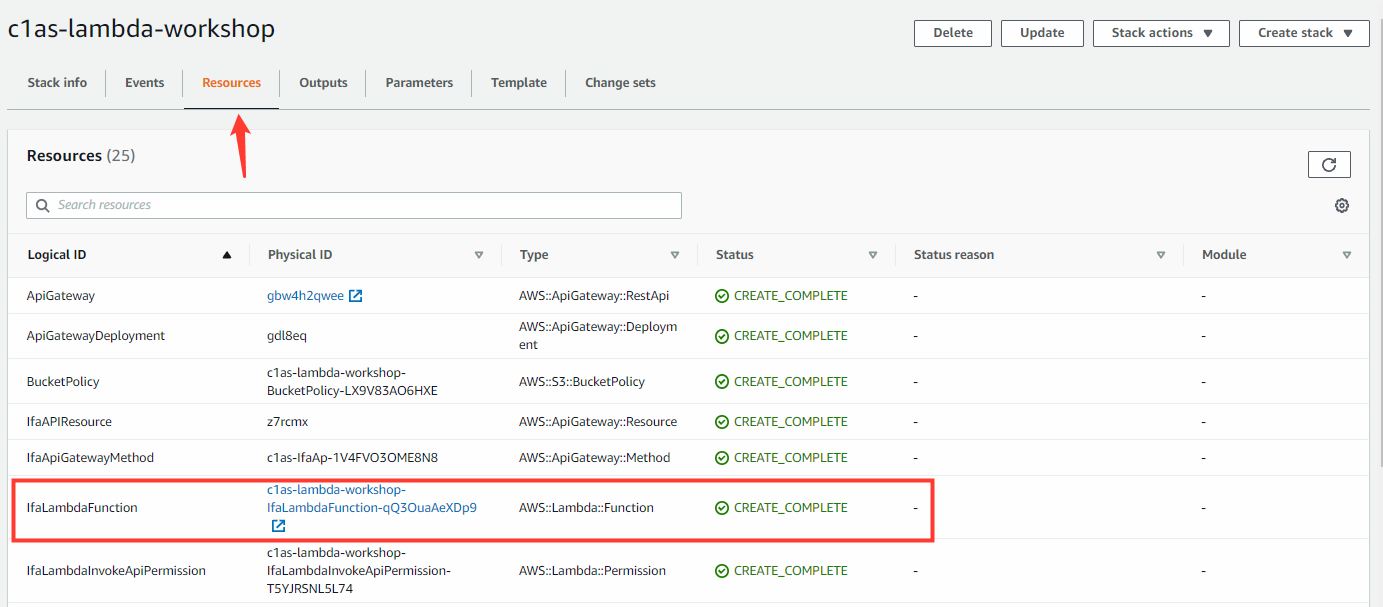
Find the Lambda layer:
To configure the agent protection layer, you need the Amazon Resource Name (ARN) for the Application Security runtime.
- In the Function Overview, select Layers

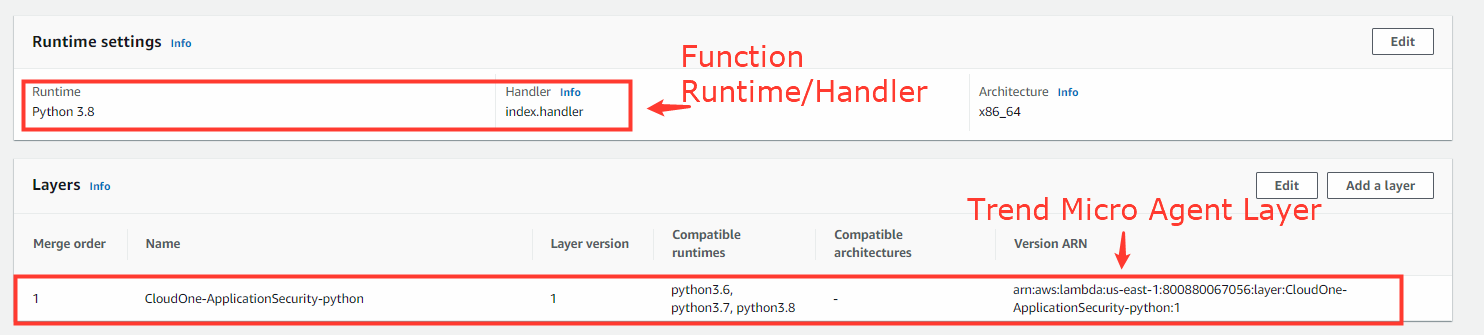
As you see above, we added the Application Security agent layer specific to Python:
- arn:aws:lambda:<‘aws region’>:800880067056:layer:CloudOne-ApplicationSecurity-python:1
For Lambda protection, Application Security provides support for both Python and NodeJS. See more here
For the Application Security layer to protect your function, some environment variables need to be added to the Lambda configuration.
To deploy the CloudFormation template, these parameters are required for a successful agent connection.
- On the IfaLambdaFunction overview page, select the Configuration tab
- Select Environment variables
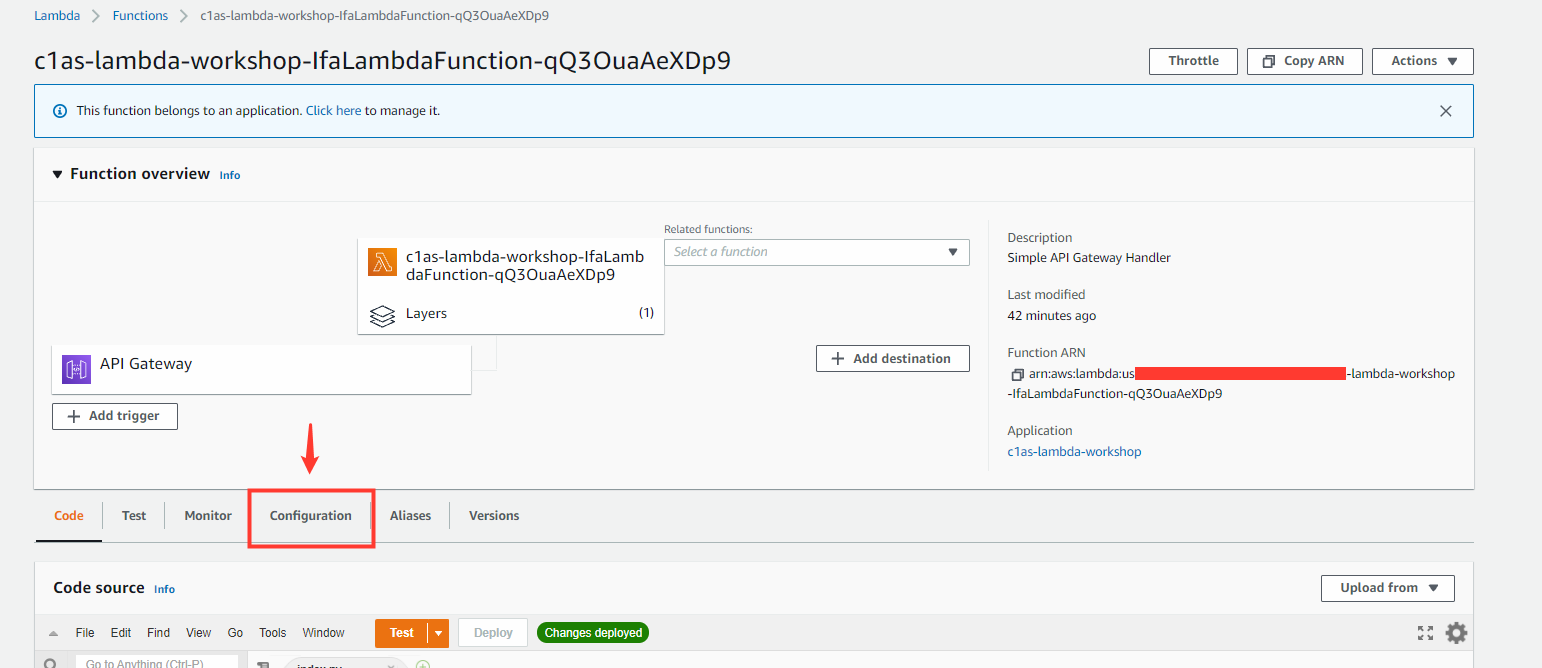
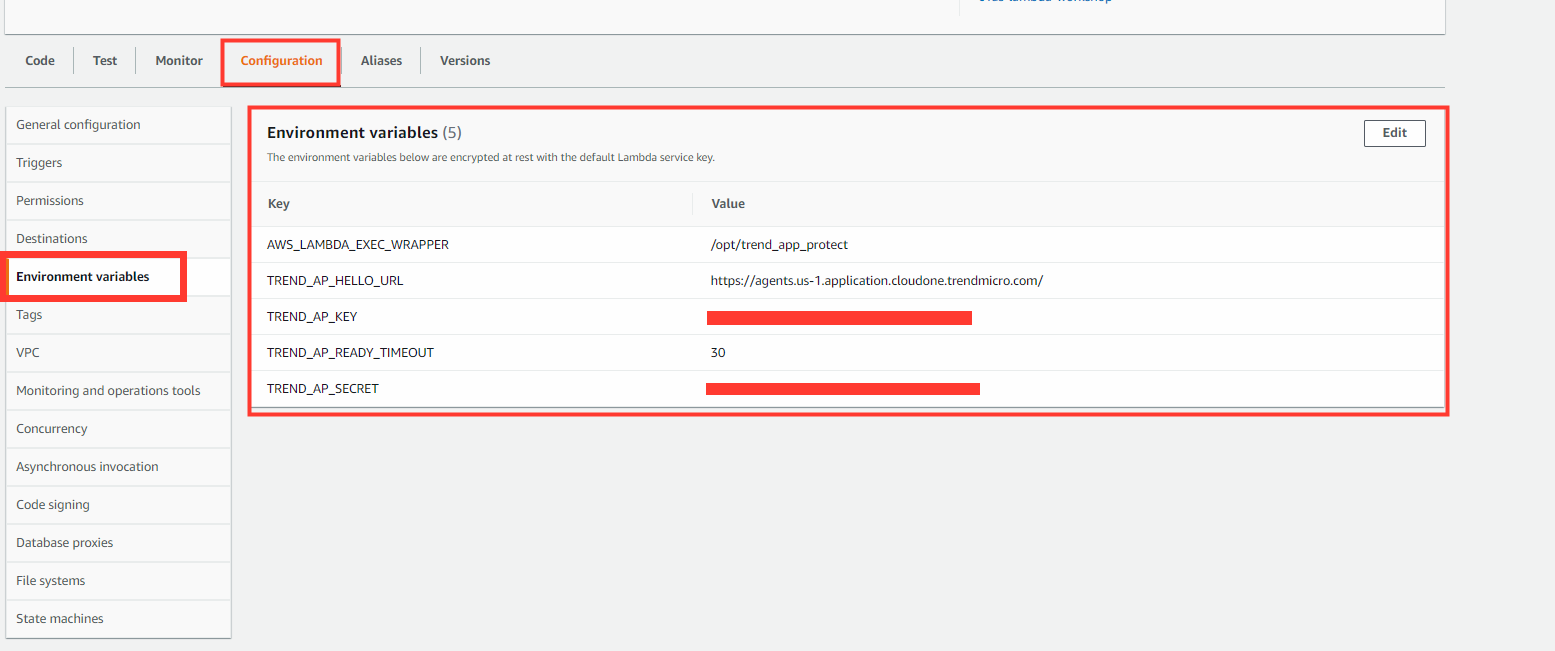
For advanced Lambda configuration please see our documentation here
Navigate back to the website URL and refresh the page a few times to allow the agent to activate for the first time.
- Go to your Application Security Console
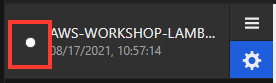
- To determine if agent is active, use the indicator light next to the security group
Inactive (White or grey light)
- White: Not Connected
- Grey: Inactive
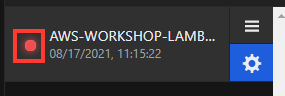
Active (Red, green or yellow light)
- Red: Connected with ongoing attack
- Yellow: Connected with previous attacks in last hour
- Green: Connected with no attacks currently
The Lambda function will only show as active when it is being used or triggered to process an event. The status light will be remain inactive (grey) until a request is made, triggering the Application Security agent
