Malicious File Upload
Malicious file upload is a method when invalidated files are uploaded on vulnerable servers, they can execute malicious script on the server-side to either upload phishing pages that extract users’ data, grant access to other illegal software, or gain control of the server to scrape valuable data. This policy scans for any malicious files potentially uploaded to your application, checks the file size, and blocks it based on the threshold provided by you.
If your application allows file uploads, attackers could upload malicious files that compromise your system.
Application Security leverages Trend Micro Smart Scan as well as the ATSE to protect your application from malicious file uploads by scanning uploaded files for malware and restricting the size of uploaded files.
1. On the JumpBox desktop locate a folder named Immersion_files. An EICAR file should be there already if not go to EICAR and obtain the file for a simple test of anti-malware capabilities.
Currently the agent’s security policy is set in report mode.

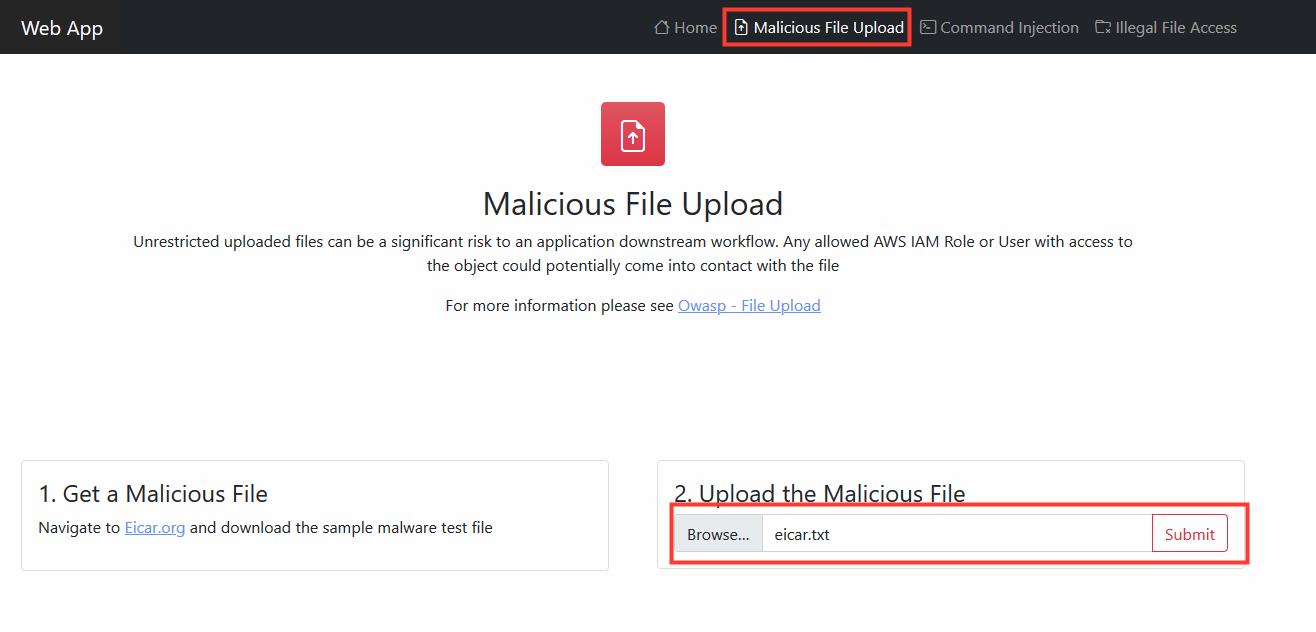
3. In your application, choose Malicious File Upload:
- Select the EICAR file saved
- Submit
4. Check the Application Security dashboard for any events.
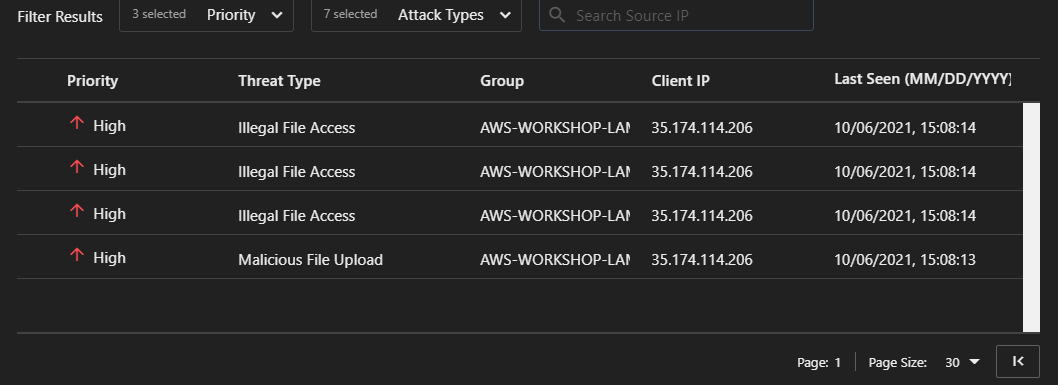
5. From the above image, two different threat types were identified.
- Select the Illegal File Access to display additional details.
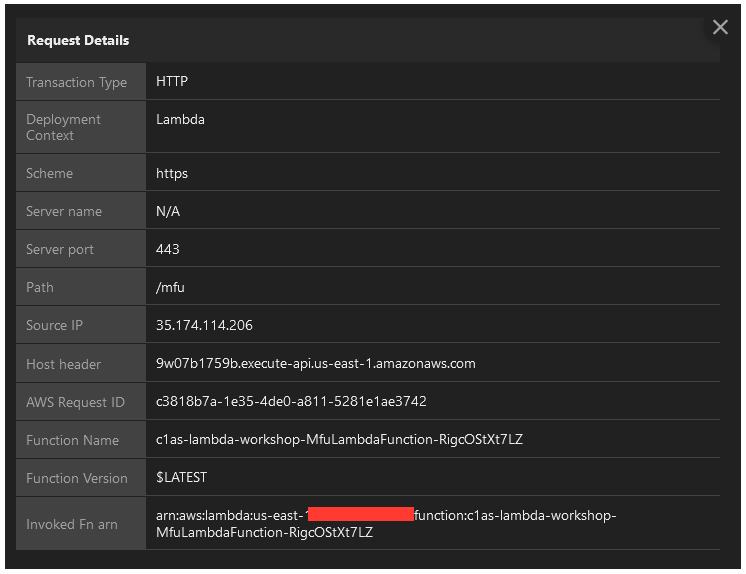
- Examine the Request Details and Illegal File Access Details


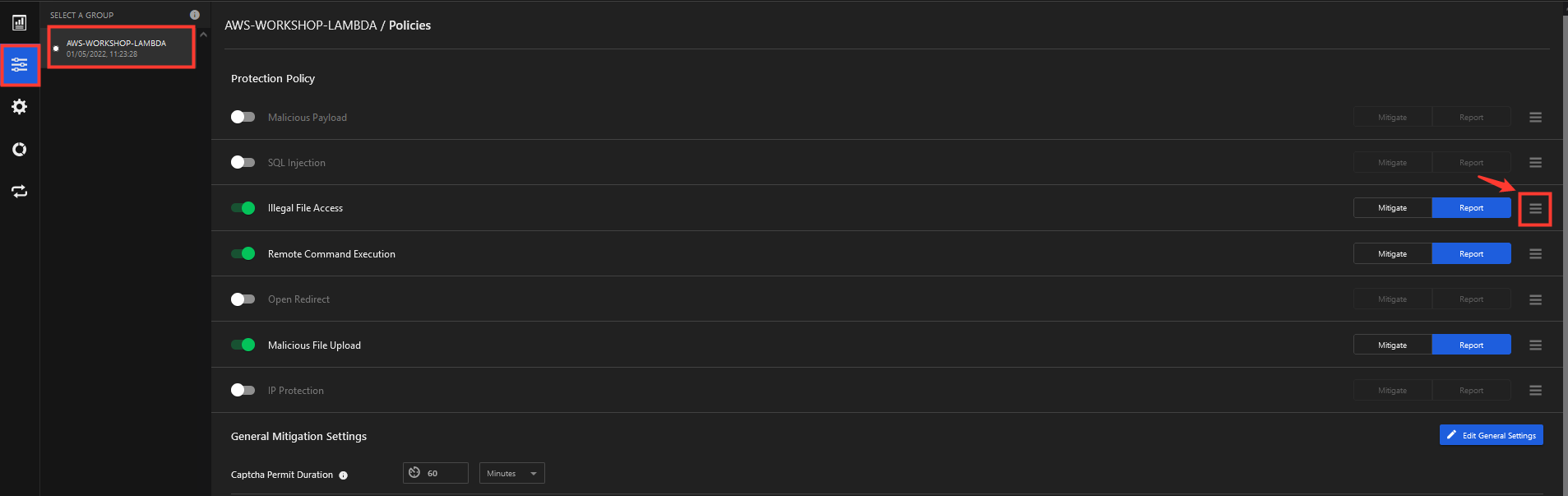
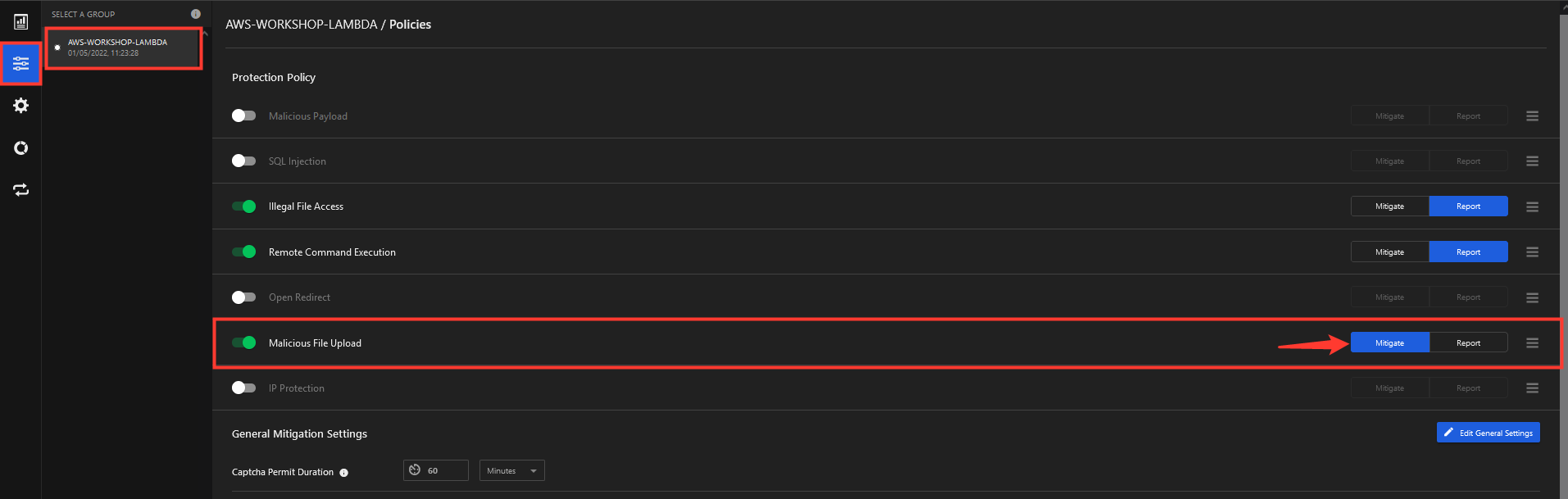
6. Make an exception in the policy under Illegal File Access
- Select AWS-WORKSHOP-LAMBDA -> Policies
- Configure Policy
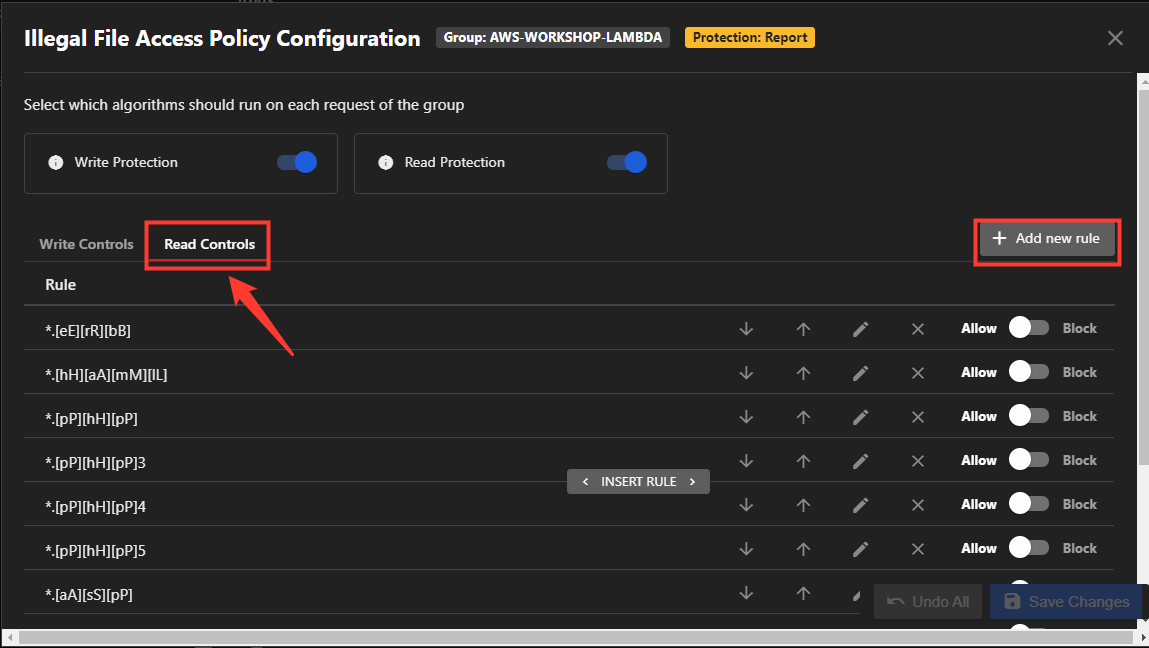
- Select tab Read Controls
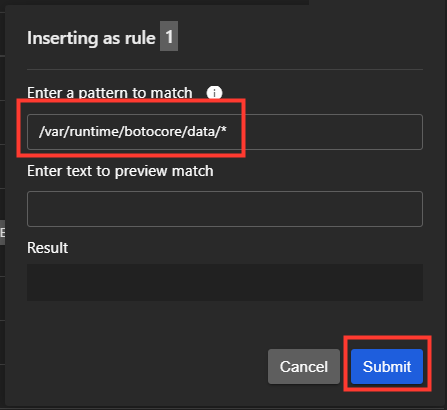
- Add Rule
/var/runtime/botocore/data/*- Submit Rule and Save Changes
7. Select the Malicious File Upload event to see the details of the request.
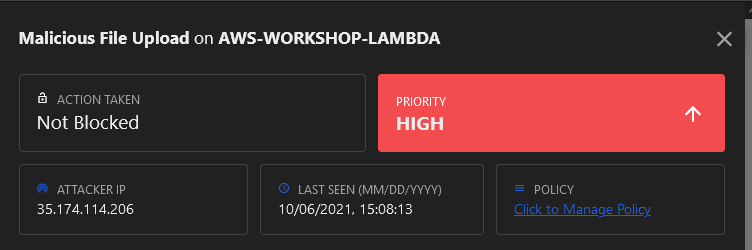
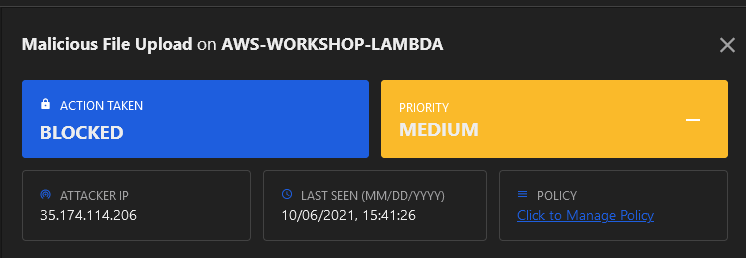
8. Change the Malicious File Upload mode to Mitigate.
9. Navigate back to the website URL and refresh the webpage. Repeat the eicar file upload process.
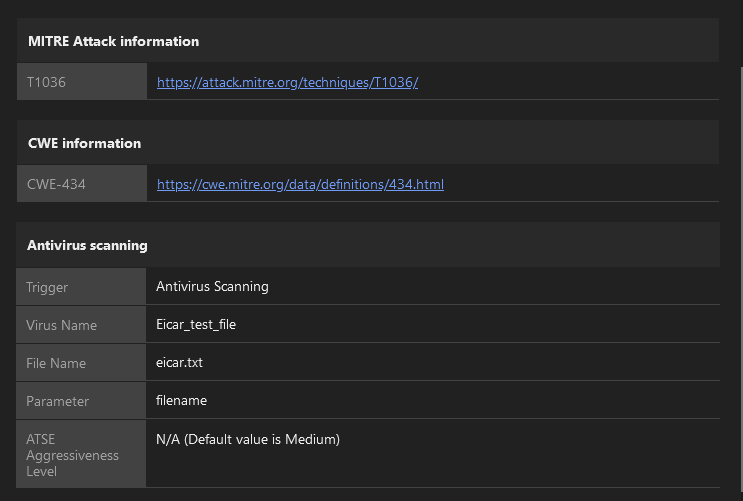
10. In the Trend Micro Cloud One console, you can see the malicious file upload was blocked. Under the Antivirus scanning section, you can view detailed information regarding the malware.