Illegal File Access
Application Security protects your application against illegal file access by blocking attackers from reading or writing to your private or sensitive files.
- With Remote Command Execution protection in Report mode, we can gather information regarding the vulnerability.
In your Lambda application command injection
- The Lambda provides a feature to perform a name server lookup on the given domain.
- Click Start Lab to be taken to the lambda function
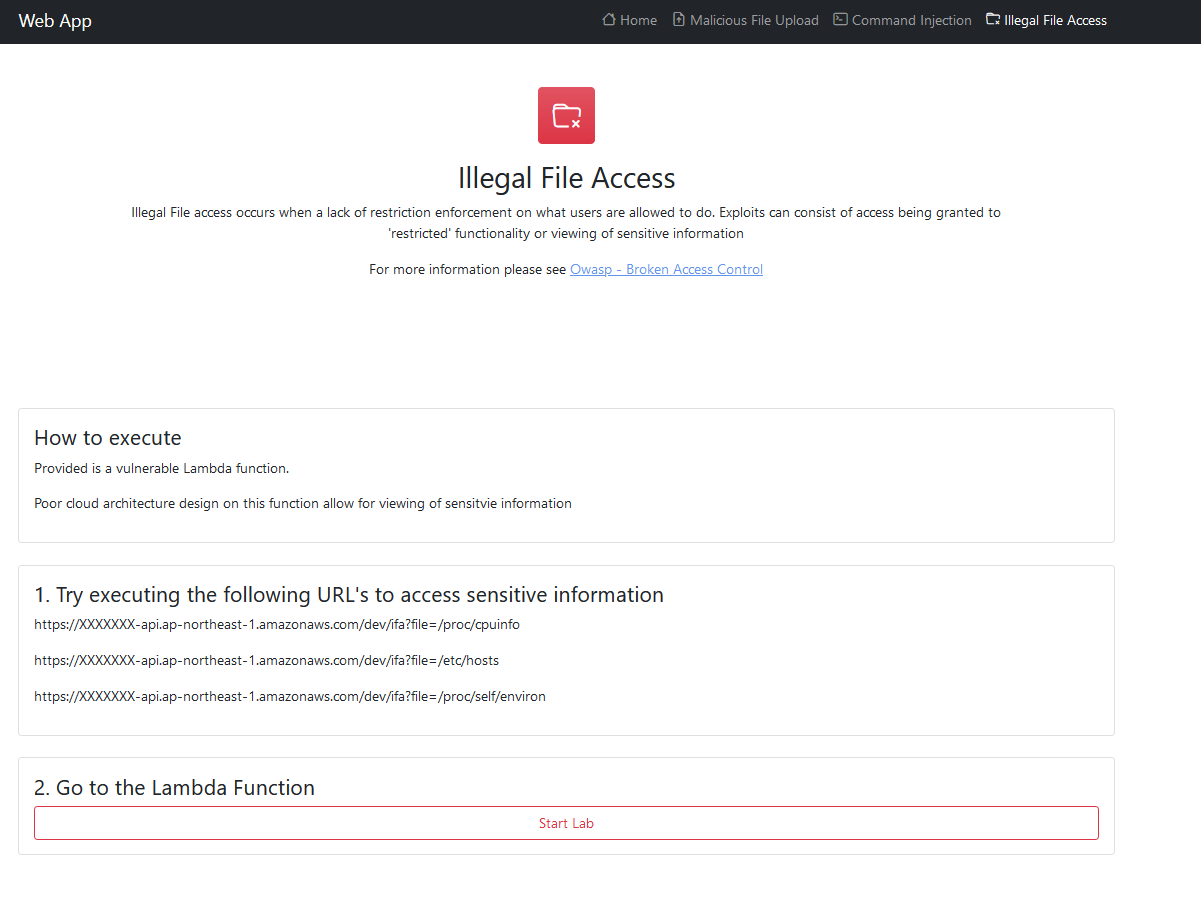
How to exploit
Manipulate the browser URL using one of the options below:
https://XXXXXXX-api.ap-northeast-1.amazonaws.com/dev/ifa?file=/proc/cpuinfohttps://XXXXXXX-api.ap-northeast-1.amazonaws.com/dev/ifa?file=/etc/hostshttps://XXXXXXX-api.ap-northeast-1.amazonaws.com/dev/ifa?file=/proc/self/environ

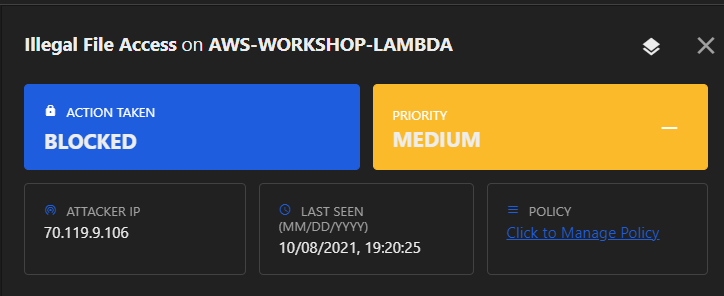
Check the Application Security console if any new event occurred.
Leveraging Request Details (under the illegal file access event) you can see what file is trying to be accessed depending on the attack executed.
/proc/cpuinfo/etc/hosts/proc/self/environ
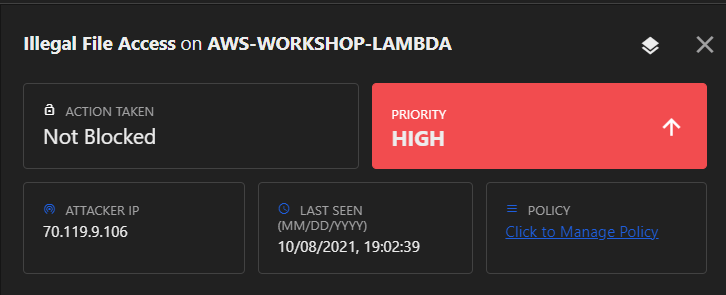
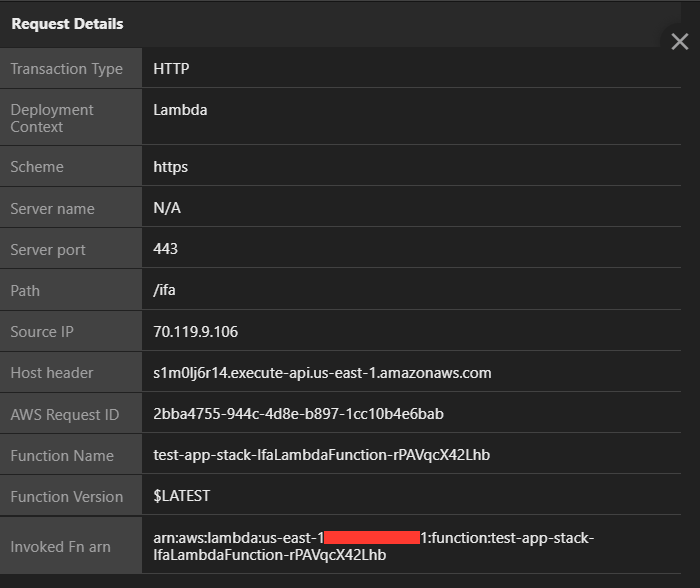

Now that you have detected an attack, modify the policy to mitigate subsequent remote command attacks from occurring.
- In your Cloud One - Application Security console.
- Select your security group AWS-WORKSHOP-LAMBDA
- Configure the Illegal File Access to Mitigate

Repeat the attack with the new changes made to the agent policy.
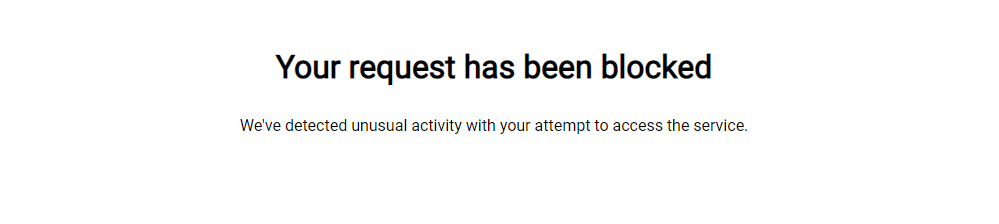
Once you attempt the exploit again your request to the application will be intercepted and blocked. Also, in your console you are still alerted to the attack time it will note the Blocked action taken by the agent.